Tips To Fine Tune APT
- # if you are looking for a debian package which mentions a particular text in its description, you can browse through all the package descriptions you have already downloaded (using apt-get update) using apt-cache, e.g., if you were looking for a debian package which provides the perl module Date::Calc, you could execute
apt-cache search "Date::Calc"
to find libdate-calc-perl
# have a look at http://newbiedoc.sourceforge.net/tutorials/apt-get-intro/info.html.en for more of these tips...
- # apt-get may run out of room (e.g., reporting something like ``E: Dynamic MMAp ran out of room''). I usually solve this type of problem by changing the cache-limit in /etc/apt/apt.conf to make it look as follows:
APT::Cache-Limit 141943904;
- # looking for a package which includes a key word in its description:
apt-cache search keyword
- # read the apt HowTo and the dselect for beginners guide if you are not yet familiar with apt (the advanced package tool) and its user interface dselect
- # have a look at apt-pinning if you want to mix stable, testing and unstable debian packages sources given a mostly-stable debian system. It basically says: install /etc/apt/preferences and include stable/testing/unstable mirrors in your /etc/apt/sources.list, and install non-stable packages using
apt-get -t unstable install whatever.package
Caveat: if you include unstable debian packages in your /etc/apt/sources.list, and you use dselect, you will automatically downgrade your machine to an unstable release... If you include references to unstable packages in your /etc/apt/sources.list, you should not use dselect, but stick to apt-get install -t {stable|testing|unstable} package.
- # edit your /etc/apt/sources.list and /etc/apt/preferences (apt-pinning is for advanced users only!! If you do not know what apt-pinning is, you should not touch /etc/apt/preferences) if necessary (e.g., commenting out lines which you do not like or which you do not need. Have a look at the optimize the /etc/apt/sources.list file section to fine tune the /etc/apt/sources.list for your geographic location). Once you have configured your /etc/apt/sources.list, you can refresh your system's database with available debian packages:
apt-get update
- # optimizing the /etc/apt/sources.list file: determine the content of /etc/apt/sources.list which fits best to your location, using, e.g.,
for a in stable testing unstable; do netselect-apt $a; mv sources.list sources.list.$a; done
- # if you wish to setup a local mirror of debian packages in a directory, say /data/debian.packages, you have to generate a Packages and Packages.gz file so that apt-get and dselect can find these packages. Include the following line
deb file:///data/debian.packages ./
in your /etc/apt/sources.list (put the line somewhere in the beginning of the sources.list file: order is important... Packages are downloaded `first seen first fetched'). The following commands create the Packages and Packages.gz files:
cd /data/debian.packages;dpkg-scanpackages . /dev/null > Packages;gzip -9c Packages > Packages.gz
|

|
Ati Drivers
 |
ati drivers, provides the video drivers you need for various operating systems. Select Linux, FireGL, Mobility FireGl T2 to configure X for the video card shipped with an HP compaq nw8000 |
|

|
Tips For Awk
- # prepend and append some text on each line of a text file:
awk '{print "prefix "$1" postfix"}' input.txt > /tmp/output.txt
- # replace the value of the second column in file1.dat by zero if it is strictly less than 0.1 (cfr., the gnuplot manual):
awk '{print $1,($2<0.1) ? 0.0 : $2}' file1.da
- # multiply the numeric value of the second column in file1.dat by five if the value of the first column is in the range of [1,3] (cfr., the gnuplot manual):
awk '{print $1,($1<=3 && $1>=1)? $2*5 : $2}' file1.dat
|

|
Tips For The Basic Unix Tools
- # text processing:
- # convert characters from lower to upper case:
fortune | tr [:upper:] [:lower:]
- # finding out how many times a particular item, in this case a dot, occurs on a text line
for a in `cat /tmp/file.txt`; do
nof=$[`echo $a|sed s/'\.'/'\n'/g|wc -l` -1]
echo a . occurs $nof times in $a
done
- # unescaping escaped text/html/javascript/... found in a file $LOGFILE:
cat $LOGFILE|sed s/+/' '/g|sed s/%0D%0A/" -- "/g|sed s/%20/" "/g|sed s/%21/'!'/g|\
sed s/%22/'"'/g|sed s/%23/'\#'/g|sed s/%24/"$"/g|sed s/%25/"%"/g|sed s/%26/"\&"/g|sed s/%27/"'"/g|\
sed s/%28/'('/g|sed s/%29/')'/g|sed s/%2A/'*'/g|sed s/%2B/'+'/g|sed s/%2C/','/g|sed s/%2D/'-'/g|\
sed s/%2E/'.'/g|sed s/%2F/'\/'/g|sed s/%3A/':'/g|sed s/%3B/';'/g|sed s/%3C/'<'/g|sed s/%3D/'='/g|\
sed s/%3E/'>'/g|sed s/%3F/'?'/g|sed s/%40/'@'/g|sed s/%5B/'['/g|sed s/%5C/'\\'/g|sed s/%5D/']'/g|\
sed s/%5E/'^'/g|sed s/%5F/'_'/g|sed s/%60/'`'/g|sed s/%7B/'{'/g|sed s/%7C/'|'/g|sed s/%7D/'}'/g|\
sed s/%7E/'~'/g|sed s/%D3/'<'/g
- # a very nice overview of commonly used text processing commands can be found at http://www.tldp.org/LDP/abs/html/textproc.html
- # remove all blank lines from a file:
grep -v '^$' input.txt > output.txt
- # count the number of newlines, words and bytes in a text file:
wc input.txt
- # reverse all the lines in a file:
rev file.txt
- # file processing:
- # dog is an enhancement of cat
- # count the number of times a particular character (in the example a comma) occurs in some file:
cat file.txt | tr -c -d ',' | wc -c
- # character set translator -- translates character sets from one encoding to another (utf-8, ascii, iso 8859-[123456789], unicode, msdos,...):
tcs
- # make a hexdump or do the reverse:
xxd file > file.hex
xxd -r file.hex > file.bis
- # dump a file byte per byte using octet, decimal, hex or binary notation:
od -j 2 -t x1 file > file.hex
- # replace all spaces in all relevant file names by underscores:
find . -name \*' '\* -exec rename s/' '/_/g "{}" \;
- # strip the path from a filename, or the last part of an absolute path:
basename extendedFilename; dirname extendedFilename
- # find all files that are between 100 and 50 days old:
find . -mtime +50 -mtime -100 -daystart
- # process processing:
- # redirect stderr to stdout:
buggyProg 2>&1
- # redirect stdout to stderr:
buggyProg 1>&2
- # redirect both stderr and stdout to a file:
buggyProg &> file
|

|
Cdvd Writers
CD/DVD Tips And Tricks
- # use the program xine-check to determine whether your cd/dvd software (e.g., mplayer, ogle, xine,...) is configured optimally:
xine-check
- # enable dma for your dvd player:
sudo hdparm -d1 -X34 /dev/dvd
If you are satisfied with this setting, consider appending its specification to /etc/init.d/bootmisc.sh:
echo hdparm -d1 -X34 /dev/dvd|sudo bash -c "cat >> /etc/init.d/bootmisc.sh"
- # the program k3b, part of the kde tools, provides a very nice user interface for writing cds and dvds:
k3b
- # how to write bootable cd/dvd images to cd/dvd using linux: here
- # create an exact copy of the information on a cd/dvd to your hard disk:
sudo umount /dev/cdrom;sudo dd if=/dev/cdrom of=/tmp/image.iso conv=noerror
- # how to burn a DVD-Video under Linux with mkisofs and dvdrecord
|

|
Tips To Write/burn Cds
- # initialize the variable ISO_DATA which points to the information you wish to write to a cd/dvd, and the variable ISOFILE which specifies name and location for the cd/dvd image:
export ISO_DATA=/home/$USER
export ISOFILE=/tmp/image.iso
sudo ls -al $ISOFILE
- # create the iso image, write it to $ISOFILE and make it contain all files found in $ISO_DATA (including all subdirectories):
mkisofs -J -r -o $ISOFILE -R $ISO_DATA
- # test the newly created iso image (optional step):
sudo mount -t iso9660 -o loop,ro $ISOFILE /cdrom
ls -alR /cdrom
sudo umount /cdrom
- # find out which cd/dvd writer can be used:
export CDWRITER=`sudo cdrecord -scanbus|grep RW|head -1|cut -f2`
if [ :$CDWRITER: == :: ];then
export CDWRITER=`sudo cdrecord -scanbus|grep DVDRAM|head -1|cut -f2`
fi
if [ :$CDWRITER: == :: ];then
export CDWRITER=`sudo cdrecord -scanbus|grep SD-R2512|head -1|cut -f2`
fi
if [ :$CDWRITER: == :: ];then
export CDWRITER=0,0,0
echo REMARK: your cd writer device could not be detected automatically...
echo REMARK: using $CDWRITER as default device...
echo REMARK: check whether your default device behaves properly with:
echo sudo cdrecord -scanbus
fi
echo we will be using device :$CDWRITER: to write your cd/dvd to...
- # if you wish to clean an existing cd/rw, you can burn the data with:
time sudo cdrecord dev=$CDWRITER -blank=fast -v -eject $ISOFILE
- # if you are using a blank cd/rw, you can burn the data with:
time sudo cdrecord dev=$CDWRITER -v -eject $ISOFILE
|

|
Tips To Burn Dvds
- # how to burn a DVD-Video under Linux with mkisofs and dvdrecord
- # how I burn the information found in $DATA_FOR_DVD on a dvd+rw using linux (and a sony dvd/cd rewritable drive unit model dru-500ax which is found at /dev/dvd):
- # specify where the information for the DVD can be found, where the temporary iso file can be stored, and the name of the DVD iso image:
export DATA_FOR_DVD=/tmp/dvd
- # clean the dvd+rw:
sudo dvd+rw-format -force /dev/dvd
- # perform the writing (master and burn an iso9660 volume):
growisofs -speed=2 -r -T -multi -overburn -Z /dev/dvd $DATA_FOR_DVD
- # append more data to an already mastered volume (make sure to use the same options for both initial burning and following sessions):
growisofs -speed=2 -r -T -multi -overburn -M /dev/dvd $DATA_FOR_DVD
- # perform the writing of a pre-mastered iso9660 volume to a dvd:
growisofs -speed=2 -dvd-compat -r -T -multi -overburn -Z /dev/dvd $DATA_FOR_DVD
|

|
|

|
|
Configurations

|
Curl
# It may happen that you have to present a userid/password before your Internet service provider configures your network settings (e.g., ip address), e.g.,
curl -d "uid=userid&pwd=whatever" https://netlogin.kuleuven.be/cgi-bin/weblogin.cgi|mail root
# Once you are satisfied with this command (it may be that your internet service provider uses other variable names (than uid and pwd) in the network login form), you can launch it after a reboot by appending it to /etc/init.d/bootmisc.sh.
# If your ISP goes down from time to time, and you need to relogin each time, you may consider running a the following command:
while date;do \
echo starting curl;\
curl -d "uid=userid&pwd=whatever" https://netlogin.kuleuven.be/cgi-bin/weblogin.cgi|mail root;\
date;\
while ping -c 10 www.google.com;do\
echo pings were successful;\
sleep 600;\
done;\
sleep 5;\
done
|

|
Tips To Use Cvs
- # checkout of a cvs module from a cvs server with respect to a particular date:
cvs -z3 -d :pserver:cvs@cvs.server.org:/pub/cvsroot checkout -D "month dd yyyy" module
|

|
Tips To Finetune When Your Daemons Start And Stop Providing Their Services
- # install and execute ksysv:
sudo apt-get install ksysv
sudo ksysv
|

|
Tips To Set Up A Simple Dhcp Server
|
dhcp server:
- # edit /etc/dhcp3/dhcpd.conf so that it contains a working configuration for the ethernet interface you wish to serve dhcp requests on, say eth0:
subnet 10.5.5.0 netmask 255.255.255.0 {
range 10.5.5.10 10.5.5.30;
option domain-name "whatever.domain.org";
option domain-name-servers dns1.whatever.domain.org, dns2.whatever.dommain.org;
}
- # specify which network interface the dhcp server should listen to by editing /etc/default/dhcp3-server:
INTERFACES="eth0"
- # restart the dhcp daemon:
sudo /etc/init.d/dhcp3-server restart
# make sure to set the subnet, netmask and range to values which are compatible with your interface settings... Have a look at /var/log/syslog to see whether you have configured your configuration files properly:
sudo tail -f /var/log/syslog &
|

|
Tips To Use Diff And Patch
- # the following command produces (given two source trees ~/original/sources and ~/updated/sources) an overview of the differences between these two trees:
cd ~/original/sources
tar -xzvf ~/whatever.tgz
cd ~
diff -ruN original/sources updated/sources > how.to.patch.original.sources
- # the following command produces, given the original source tree and the differences between the original and updated sources, updated sources:
cd ~/current/sources
tar -xzvf ~/whatever.tgz
patch -p2 < how.to.patch.original.sources
|

|
Tips For Dselect
- dselect (`man dselect` is your friend, or read the excellent article on using debian: http://www.linuxgazette.com/issue15/debian.html) is not the most user-friendly program around. It is normal that it reports a few errors as it operates in several rounds: in the first round, all packages that are required or used by other packages are unpacked and configured. Packages that rely on some of those are only unpacked, not yet configured as this will happen in the subsequent round. It is perfectly possible that the completion of this iterative process takes several rounds if many packages have to be installed/upgraded.
If you are using a low-bandwidth connection (downloading the commonly selected packages for a new complete installation may easily take one hour given a 100 KB/sec-Internet connection), it may be advisable to copy the debian packages apt-get downloads to a safe place for later usage:
mkdir -p /data/debian.packages;
cp /var/cache/apt/archives/*.deb /data/debian.packages
You may also wish to follow the procedure to set up a local mirror of these packages which can be used by dselect later on.
|

|
Setting Up An Encrypted Filesystem
- # http://loop-aes.sourceforge.net/loop-AES.README
- # Encryption HOWTO
- # Encrypted Root Filesystem HOWTO
- # Cryptoloop HOWTO
- # Setting up the Cryptographic FileSystem (cfs):
- # setting the thing up:
- # install the cfs package:
sudo apt-get install cfs
- # create /etc/exports if it does not yet exist to avoid cfsd's complaints:
sudo touch /etc/exports
- # start the cfs daemon:
sudo /etc/init.d/cfsd restart
- # using the stuff:
- # prepare the creation of an encrypted directory called "~/encrDir":
cmkdir ~/encrDir
# the cmkdir command prompts for a strong passphrase (of at least 16 characters)
- # make this directory available to the user with that password:
cattach ~/encrDir decrypted
# the cattach command prompts for the passphrase that was used to create the directory ~/encrDir # once completed, the directory /crypt/decrypted becomes available wherein one can edit all files in plaintext
- # once you finish editing the decrypted data, this directory should be unmounted:
cdetach decrypted
# note that the content of the directory ~encrDir is at all times encrypted. The plaintext is only available to the user who presented the correct passphrase
|

|
|
Howto To Enable The Wheel Mouse In Emacs

|
Tips To Configure The Mail Transport Agent Called Exim
|
# exim
# Exim is a mail transport agent (MTA) developed at the University of Cambridge. It is easy to configure and does its job as expected.
- # install exim
sudo apt-get install exim
- # execute the exim configuration tool
sudo eximconfig
- # select 3: satellite system
- # enter the hostname of the machine you are configuring. Example: if your machine is hostname.domain.org, you should enter hostname.domain.org
- # enter the domain name of your email address when asked where the users will read their email. E.g., if your email address reads userid@domain.org, you should enter `domain.org'
- # enter the mail server's hostname as the smarthost to handle outgoing mail, e.g., smtp dot kulnet dot kuleuven dot ac dot be
- # enter the userid of the user who should receive the email sent to root
- # accept to overwrite the /etc/aliases file (or reject, this is up to you)
- # read very carefully what the configuration tool shows you for its configuration! accept the configuration if it is ok, restart the procedure if not...
- # once you have accepted the configuration file, you should check the /etc/aliases file. Make sure that this file does not contain any `real-userid' items... Replace all these occurrences with valid email addresses.
- # test whether you changed all real-userid occurrences:
grep real- /etc/aliases
- # once the /etc/aliases file does no longer contain any real-userid items, you can test your mail delivery system:
echo piep sent at `date` from `hostname`|mail userid@domain.org
|

|
Preferred FireFox Extensions
 |
basics, adds a 'new tab' button to the tab bar |
 |
clear http auth, clears the http authentication data stored by the browser |
 |
extension uninstaller, by far the most important extension to install if combined with the extension uninstaller api :)) |
 |
extension uninstaller api, required extension for the extension uninstaller gui |
 |
forecastFox is a highly customizable firefox extension that brings weather forecasts to your firefox browser |
 |
mime type editor, standalone extension for FireFox to administer helper applications to start based on data's mime type |
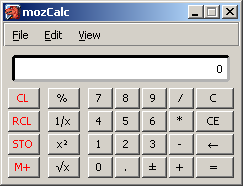 |
mozCalc, an easy to use xul calculator, provides normal, scientific, reverse polish notation modes |
 |
open download, adds an additional option in the download dialog allowing you to open the file using the default program assigned by your operating system |
 |
plain text links, allows you to select text and treat it a link |
 |
quick note, a nice extension to quickly jot down notes, e.g., in a separate window or a in a FireFox sidebar |
 |
reloadEvery, reloads a tab every so many seconds |
 |
sessionSaver, remembers loaded tabs and their history items when FireFox is manually closed when next restarted |
![tab browser extensions</a>, provides an advanced configuration tool for the tabs bar. This extension can place the tabs bar at the bottom of the browser, which makes FireFox look and behave much like opera ];-) tab browser extensions</a>, provides an advanced configuration tool for the tabs bar. This extension can place the tabs bar at the bottom of the browser, which makes FireFox look and behave much like opera ];-)](../../images/tabBrowserExtensions.png) |
tab browser extensions, provides an advanced configuration tool for the tabs bar. This extension can place the tabs bar at the bottom of the browser, which makes FireFox look and behave much like opera ];-) |
 |
translation panel, translates input text into a foreign language. After the extension has been installed (and you have restarted FireFox), you can open the translation panel (view, sidebar, translation panel). If no languages are available (this happens quite frequently with a new install), you can solve this by unzipping the translationpanel.*.xpi which you installed, and by manually importing the items.rdf as follows: select setting, and inport/export (sic), select import, go to the directory where you unzipped the *.xpi file, and open the items.rdf file. Using this nice tool furtheron is rather straightforward |
 |
trivial, provides the toolbar buttons I have been looking for for ages... close tab, toggle full screen, cut, copy, paste, etc. |
 |
web developer, provides a huge set of development features to the browser, e.g., a java console, html validator, and much more |
 |
mozImage, a simple image browser with slide show features and the ability to scale images to window size |
 |
mozilla Archive Format, allows complete web pages to be saved in a single archive file. The original url of the page and date/time the page was put in the archive are stored in the archive |
 |
things they left out, provides the things they left out in the design of FireFox, e.g., panels for languages, mime types, security certificates, find as you type, etc. (this extension does not work for me, but it may for you :))) |
 |
tipBar, adds a bar to the bottom of the content window that shows tips |
|

|
Tips To Set Up firewire Devices
Enabling FireWire support for an external hard disk:
- # load the appropriate modules:
echo ieee1394 >> /etc/modules-`uname -r` # FireWire protocol
echo ohci1394 >> /etc/modules-`uname -r` # Open Host Controller Interface
echo raw1394 >> /etc/modules-`uname -r` # Serial Bus Protocol-2
echo usb-storage >> /etc/modules-`uname -r` # generic usb support for storage devices
- # check whether the device is present according to your machine:
sudo gscanbus
- # if the device is not yet present, you might need to execute the utility from http://www.garloff.de/kurt/linux/rescan-scsi-bus.sh to look for new scsi devices:
cd /usr/local/bin
wget -N --retr-symlinks http://www.garloff.de/kurt/linux/rescan-scsi-bus.sh
sudo sh /usr/local/bin/rescan-scsi-bus.sh
- # list the partitions which are currently known to your machine with:
sudo sfdisk -l
|

|
Grep Tips To Efficiently Find What You Are Looking For In Text Files
- # agrep provides an approximate grep
- # searching for specific patterns using grep and regular expressions (mostly copied from http://www.robelle.com/library/smugbook/regexpr.html):
- # the theory:
^ (Caret) = match expression at the start of a line, as in ^A.
$ (Question) = match expression at the end of a line, as in A$.
\ (Back Slash) = turn off the special meaning of the next character, as in \^.
[ ] (Brackets) = match any one of the enclosed characters, as in [aeiou].
Use Hyphen "-" for a range, as in [0-9].
[^ ] = match any one character except those enclosed in [ ], as in [^0-9].
. (Period) = match a single character of any value, except end of line.
* (Asterisk) = match zero or more of the preceding character or expression.
\{x,y\} = match x to y occurrences of the preceding.
\{x\} = match exactly x occurrences of the preceding.
\{x,\} = match x or more occurrences of the preceding.
- # examples:
cat -v -e -t dump # show non-printing characters too
grep BOB tmpfile # search 'tmpfile' for 'BOB' anywhere in a line
grep -i -w blkptr * # case insensitive search all files in the current directory for the word blkptr
grep run[- ]time *.txt # find 'run time' or 'run-time' in all txt files
grep smug files # search files for lines with 'smug'
grep '^smug' files # 'smug' at the start of a line
grep 'smug$' files # 'smug' at the end of a line
grep '^smug$' files # lines containing only 'smug'
grep '\^s' files # lines starting with '^s', "\" escapes the ^
grep '[Ss]mug' files # search for 'Smug' or 'smug'
grep 'B[oO][bB]' files # search for BOB, Bob, BOb or BoB
grep '^$' files # search for blank lines
grep '[0-9][0-9]' file # search for pairs of numeric digits
grep '^From: ' /var/spool/mail/$USER # list your mail
grep '[a-zA-Z]' # any line with at least one letter
grep '[^a-zA-Z0-9] # anything not a letter or number
grep '[0-9]\{3\}-[0-9]\{4\}' # 999-9999, like phone numbers
grep '^.$' # lines with exactly one character
grep '"smug"' # 'smug' within double quotes
grep '"*smug"*' # 'smug', with or without quotes
grep '^\.' # any line that starts with a Period "."
grep '^\.[a-z][a-z]' # line start with "." and 2 lc letters
|

|
Tips To Compute Hash Values
|
collisions for md5:
# two distinct inputs which produce an identical hash value for the infamous (broken) md5 hash function, i.e., a collision:
echo d131dd02c5e6eec4693d9a0698aff95c2fcab58712467eab4004583eb8fb7f89 > 1.asc
echo d131dd02c5e6eec4693d9a0698aff95c2fcab50712467eab4004583eb8fb7f89 > 2.asc
echo 55ad340609f4b30283e488832571415a085125e8f7cdc99fd91dbdf280373c5b >> 1.asc
echo 55ad340609f4b30283e4888325f1415a085125e8f7cdc99fd91dbd7280373c5b >> 2.asc
echo d8823e3156348f5bae6dacd436c919c6dd53e2b487da03fd02396306d248cda0 >> 1.asc
echo d8823e3156348f5bae6dacd436c919c6dd53e23487da03fd02396306d248cda0 >> 2.asc
echo e99f33420f577ee8ce54b67080a80d1ec69821bcb6a8839396f9652b6ff72a70 >> 1.asc
echo e99f33420f577ee8ce54b67080280d1ec69821bcb6a8839396f965ab6ff72a70 >> 2.asc
xxd -r -p 1.asc > 1.bin
xxd -r -p 2.asc > 2.bin
if cmp -l 1.bin 2.bin;then echo the two files are identical...;else echo the two files are different;fi
md5sum 1.bin 2.bin
# the commands above result in the following remarkable output:
1.bin 2.bin differ:
20 207 7
46 161 361
60 362 162
84 264 64
110 250 50
124 53 253
the two files are different
79054025255fb1a26e4bc422aef54eb4 1.bin
79054025255fb1a26e4bc422aef54eb4 2.bin
|

|
image Processing Tools And Tips
- # create a nice webpage with all your thumbnails:
webmagick --recurse --forcehtml --forcemontage --srcdir ~/pictures --columns 4
- # from tiff to eps (useful to include, e.g., a powerpoint slide in a LaTeX document):
convert slide.tiff slide.eps
- # very nice image manipulation program:
sodipodi
|

|
Tips To Set Up A Secure Imap Server
|
Configuring an imaps server (imap over ssl)
- # install the imap server package. This package comes with ssl support:
sudo apt-get install uw-imapd
# disable imap2 and imap3, enable imaps
- # create your own self-signed certificate, or install a commercial certificate. The certificate should be stored in /usr/lib/ssl/certs/imapd.pem, the private key in /usr/lib/ssl/private/imapd.pem. Make sure to input sensible data during the certificate generation process, as the imap client should be able to determine its trustworthiness:
cd /usr/lib/ssl/certs
openssl req -new -x509 -nodes -out imapd.pem -keyout ../private/imapd.pem -days 365
# Country Name (2 letter code) [AU]:be
# State or Province Name (full name) [Some-State]:belgium
# Locality Name (eg, city) []:city name
# Organization Name (eg, company) [Internet Widgits Pty Ltd]:organisation name
# Organizational Unit Name (eg, section) []:unit name
# Common Name (eg, YOUR name) []:secure imap server certificate, valid until XXX/XX/XXXX
# Email Address []:your.email.address@domain.org
- # you can now configure your imap client to connect to that server over ssl. Using, e.g., pine, your ~/.pinerc could look like the following to read your email in the folder ~/Mail when connecting to your imap server through SSL/TLS using yourUserid (replace yourUserid with your userid, hostname.domain.org with the hostname of your mailserver, and Mail with the directory name of your mail folder in your home directory). The example omits checking the authenticity of the imaps server's certificate:
folder-collections="secure IMAP server"{hostname.domain.org/ssl/user=yourUserid/novalidate-cert}Mail/[]
|

|
Tips To Manipulate Jar Files
- # unjar all jar files found in $JARFILES into $CLASSES:
export CLASSES=~/unjarred;
export JARFILES=.;
mkdir -p $CLASSES;
cd $CLASSES;
find $JARFILES -name \*jar -exec jar -xf {} \;
- # recursive decompilation of all class files in $CLASSES, storing their decompiled version in $DECOMPILED:
export CLASSES=~/unjarred;
export DECOMPILED=~/decompiled;
cd $CLASSES;
mkdir -p $DECOMPILED;
find -name \*class -exec jad -b -dead -o -s java -safe -ff -lnc -r -d $DECOMPILED {} \;
|

|
|
Suggestions To Configure Java Browser Plugins

|
Kernels
Installing an initrd kernel image:
- # getting the kernel images:
apt-get install kernel-image-2.4.27-1-686 kernel-pcmcia-modules-2.4.27-1-686
- # make sure your /etc/lilo.conf contains something like:
default="Linux-New"
image=/boot/vmlinuz
label="Linux-New"
initrd=/boot/initrd.img
append="ramdisk_size=100000 init=/etc/init lang=us apm=power-off nomce quiet lang=us dma desktop=icewm"
read-only
- # make sure the installer will not ask you for this check in the future:
echo do_initrd=\"Yes\" >> /etc/kernel-img.conf
- # continue the installation of the kernel image...
- # I usually install a boot block using the existing /etc/lilo.conf
- # that's it... reboot your machine and enjoy your new kernel...
|

|
Tips To Make Your LaTeX Life Easier
|
Powerpoint plugins
- TexPoint is a very nice Powerpoint add-in that enables the easy use of Latex symbols and formulas in Powerpoint presentations. It has two main modes of operation: inline and display. In inline mode you can use Latex symbol-macro invocations such as "\alpha^2 \times \beta_0" on your Powepoint slides. In the display mode you can write any Latex source and Latex is run to produce a bitmap that is then inserted on the slide. The bitmap remembers its Latex source so you can modify it later.
Graphical User Interfaces
 Kile is a user friendly Tex/LaTeX integrated editor Kile is a user friendly Tex/LaTeX integrated editor
|

|
Tips To Repair A Broken Master Boot Record Or Lilo Configuration File
- # running lilo on a machine on which the lilo.conf or (master) boot record have become inconsitent or have been overwritten:
- # boot from the Knoppix cd and open a terminal window
- # specify on which partition your crippled /etc/lilo.conf can be found, and mount it:
export PARTIT=/hda7
sudo mount /dev/$PARTIT /mnt/$PARTIT
- # copy the crippled file to a writeable location:
sudo cp /mnt/$PARTIT/etc/lilo.conf ~/
- # edit the erroneous lilo.conf to fix the problem:
sudo joe ~/lilo.conf
- # make sure to replace each occurrence of `=/boot` by `=/mnt/hda7/boot` (given that your unix operating system is stored on /dev/hda7)
- # execute lilo:
sudo ln -sf /mnt/$PARTIT/boot/ /
sudo lilo -C ~/lilo.conf
- # reboot the machine without the Knoppix cd
sudo shutdown -r now
- # remember to repair the lilo.conf again once your machine boots again...
|

|
Tips To Manipulate The Speed Settings Of Your Network Interface
|
mii-tool (media-independent interface status manipulation tool):
- # finding out which settings your network interface agreed on with your hub/router/switch/...:
sudo mii-tool
- # specify 10 mbps, full duplex:
sudo mii-tool --force=10baseT-FD eth0
- # specify 10 mbps, half duplex:
sudo mii-tool --force=10baseT-HD eth0
- # specify 100 mbps, full duplex:
sudo mii-tool --force=100baseTx-FD eth0
- # specify 100 mbps, half duplex:
sudo mii-tool --force=100baseTx-HD eth0
|

|
Tips To Configure Your Laptop's Modem
|
Basic setup of a modem in linux
Making a modem work consists of two phases: the modem device must first be made available, and then configured.
- # configuring the modem driver:
- # a modem found in, e.g., an hp compaw nw8000 laptop computer reports Modem: Intel Corp. 82801DB AC'97 Modem Controller (rev 3) when checking the output of
cat /proc/pci
This modem can be activated with a 2.6.x linux kernel once the sl-modem-daemon package is installed:
sudo apt-get install sl-modem-daemon
- # an intel modem 82801ca/cam, as can be found in a dell latitude c640:
- # locate the appropriate modem driver from the Internet:
cd /tmp;
wget http://linmodems.technion.ac.il/pctel-linux/pctel-0.9.6.tar.gz
- # unpack the stuff:
tar -xzvf pctel-0.9.6.tar.gz
- # configure the make files for your platform:
cd /tmp/pctel-0.9.6
./configure --with-hal=i8xx
- # make and install the stuff if successful:
if make;then sudo make install;else echo problem making the stuff =============;fi
- # make sure that the modem modules are loaded at boot time:
echo pctel >> /etc/modules-`uname -r`
echo ptserial >> /etc/modules-`uname -r`
- # configuring the dial in program wvdial:
- # run the configuration program (if this program does not seem to find your modem, you may have a problem which is not within the scope of this page: read the INSTALL and README files of the modem driver software, e.g., at http://linmodems.technion.ac.il/pctel-linux):
sudo wvdialconf /etc/wvdial.conf
- # Note that this program probably terminates mentioning where your modem has been found, e.g.,
Found a modem on /dev/ttyLT0, using link /dev/modem in config.
indicates that the modem device is /dev/ttyLT0
- # edit /etc/wvdial.conf to specify the phone number you wish to dial, the userid that must be used, and the password which should be presented:
joe /etc/wvdial.conf
This file typically looks like this:
[Dialer Defaults]
Modem = /dev/modem
Baud = 115200
Init1 = ATZ
Init2 = ATQ0 V1 E1 S0=0 &C1 &D2 +FCLASS=0
ISDN = 0
Modem Type = Analog Modem
Phone = <Target Phone Number>
Username = <Your Login Name>
Password = <Your Password>
- # test your modem configuration:
sudo wvdial
- # if the program claims not to be able to detect /dev/modem, you should create a symbolic link pointing to the modem device (assume /dev/ttyLT0 is reported by the wvdialconf program ):
ln -sf /dev/ttyLT0 /dev/modem
- # you can now use your modem to dial to your Internet service provider using:
sudo wvdial
Additional information
- # you can read additional information on popular modem tools at the Modem-HOWTO. This page gives tips for software to deal with fax, dialback, statistics, etc.
|

|
Tips For Mysql
- # setting the server root password:
mysql -uroot mysql
mysql>UPDATE user SET Password=PASSWORD('mysqlrootpassword') WHERE user='root';
mysql>FLUSH PRIVILEGES;
mysql>quit
- # initial setting up of diogenes:
mysql -uroot -p"mysqlrootpassword"
mysql> use diogenes;
mysql> insert into diogenes_auth set username="root",password=MD5(""),perms="admin";
mysql> quit
|

|
Network
# In case you wish to clone a MAC address on your machine, specify this address in /etc/network/interfaces:
auto eth0
iface eth0 inet dhcp
hwaddr wh:at:ev:er:ad:dr
If you wish to specify a static ip address, this would become:
auto eth0
iface eth0 inet static
address 1.2.3.4
netmask 255.255.255.x
gateway 2.3.4.5
#network 1.2.3.256-x
#broadcast 1.2.3.4
|

|
Tips To Set Up Nfs And A Secure Tunneling Solution To Mount Remote File Systems With Shfs
|
SHFS -- "Mount ANY dir from ANY host in a SECURE way"
# shfs is a very nice way to circumvent the insecurities of nfs. It can mount a remote directory on your local machine, just as one would do with nfs (shfsmount and shfsumount understand the same syntax as the normal nfs mount and umount commands, but in stead of sending the files in the clear, they are sent through an ssh tunnel)...
Installing shfs
- basic installation:
- for debian/stable (woody):
sudo apt-get install kernel-headers-`uname -r` fakeroot debhelper
cd /lib/modules/`uname -r`
sudo ln -s /usr/src/kernel-headers-`uname -r` build
mkdir /tmp/shfs
cd /tmp/shfs
wget http://kent.dl.sourceforge.net/sourceforge/shfs/shfs-0.35.tar.gz # or any other server
tar -xzvf shfs-0.35.tar.gz
cd shfs-0.35
make deb
sudo dpkg -i ../shfs*deb
sudo chmod u+s /usr/bin/shfsmount /usr/bin/shfsumount
- for debian/testing and debian/unstable:
sudo apt-get install shfs-source shfs-utils module-assistant
sudo module-assistant build shfs
sudo module-assistant install shfs
sudo modprobe /lib/modules/2.4.27/shfs/shfs.o
echo shfs >> /etc/modules
- finishing touch:
- # once the shfs system works correctly, you can add a line similar to the following to your /etc/fstab:
userid@remoteMachine:/remoteDirectory /home/userid/remoteDirectory shfs rw,user,noauto 0 0
Using shfs
- # mounting a remote directory. the --persistent flag makes the mount survive temporary connection outage by reconnecting to the server if it went down:
mkdir ~/remoteDir
shfsmount --persistent $USER@remote.machine.org:/home/$USER ~/remoteDir
- # mounting a remote home directory in nfs-replacement mode (i.e., preserving userid and groupid, making it available to all users, each user has only access to the files he/she is allowed to access, based on file/directory access permissions), and with symlink resolution (-s):
mkdir -p /fileserver/home
shfsmount -s --persistent root@remote.machine.org:/home /fileserver/home -o preserve,rmode=755
- # unmounting a mounted remote filesystem:
shfsumount ~/remoteDir
Information about nfs
- # this link provides a very nice introduction to nfs
- # figuring out what nfs version some host uses:
rpcinfo -p hostname |grep nfs
For those who really need nfs (as you should consider using shfs in nfs mode rather than nfs!)
Configuring an nfs server
- # edit /etc/exports to reflect to which nfs clients you wish to export filesystems of your nfs server. Example: you may wish to export the /home filesystem of your nfs server to an nfs client computer with a particular ipaddress. The nfs client can mount the filesystem in readwrite mode:
/home 192.168.0.100(rw)
Configuring an nfs client
- # create a mountpoint /remoteHome whereto you will mount the filesystem /home of the nfs server:
mkdir /remoteHome
- # you can now mount the file server's filesystem:
sudo mount -t nfs server.domain.org:/home /remoteHome
- # if you wish to mount the remote filesystem persistently, you can add the following line to your /etc/fstab:
echo server.domain.org:/home /remoteHome nfs defaults 0 0 >> /etc/fstab
|

|
Useful Helper Programs And Tools
- # the most useful and userfriendly introductory to unix commands, both for beginners and advanced users can be found at http://linux.about.com/?once=true&
- # flip can be used to convert text files in the current directory and below from unix format (linefeed, 0x0a, LF) to windows format (carriage return + linefeed, 0x0d0a, CRLF):
find . -type f -exec flip -d {} \;
- # flip can be used to convert text files in the current directory and below from windows format (carriage return + linefeed, 0x0d0a, CRLF) to unix format (linefeed, 0x0a, LF):
find . -type f -exec flip -u {} \;
- # clean up an html page:
tidy
- # reformat paragraphs in a text file:
par
- # reformat a text file:
fmt
- # what the fuck decodes acronyms:
wtf wtf; wtf afaik
- # one-line information on many commands and programs:
whatis whatis
- # more extensive information on a particular commands or item:
man whatis
- # helpful information on built-in commands of the current shell (most probably bash):
help help
- # fun with ascii art:
for a in /usr/share/cowsay/cows/*cow;do fortune -s|cowsay -f $a;done|less
- # and -- the auto nice daemon: automatically renices cpu-demanding processes
sudo apt-get install and
- # kile -- a very user-friendly LaTeX front-end
- # Dictionary lookup:
dict term
- # Fortune cookies matching a specific pattern:
fortune -i -m pattern
- # Gnome-based hex editor
ghex2
- # List information on all open files that belong to all active processes, the status of the modules currently available to the kernel, a quick overview (interrupts, ioports, dma) on the currently installed hardware, the currently installed pci devices, and the currently active usb devices:
lsof; lsmod; lsdev; lspci; lsusb
- # Network load overview:
netload eth0 -t 5
- # finding out which type of machine you are working on:
uname -a
- # finding out some interesting information on a particular host or machine:
nslookup -querytype=any hostname.domain.org
whois --verbose ipaddress
host -a hostname.domain.org nameserver.org
- the following link provides very useful information on various frequently used unix commands: introduction to various unix tools
|

|
Tips For Nfs And A Secure Tunneling Solution To Mount Remote File Systems With Shfs
|
Configuring a nis client
- # configure the shadow, passwd and group files:
echo +:::::::: >> /etc/shadow
echo +:::::: >> /etc/passwd
echo +::: >> /etc/group
- # set the identification string of your nis domain:
echo nisServerIdentificationString > /etc/defaultdomain
- # set the ipaddress of the nis master (remember that nis does not perform dns queries):
echo ypserver your.nis.server.domain.org > /etc/yp.conf
- # install the nis package:
sudo apt-get install -y nis
- # start the nis daemon:
sudo /etc/init.d/nis restart
- # you can now test whether the stuff works by requesting the possible userids which your nis server provides:
ypcat passwd
|

|
Tips To Mount Your ntfs Read/write
- # with the following command you prepare your knoppix 3.4 (and higher) machine to mount an NTFS partition readwrite. This command has to be executed only once:
sudo captive-install-acquire
- Press the ``forward'' button twice to start scanning your harddisk for native ntfs drivers. After a few minutes, the program may crash (i.e., the program crashes on my machine), but this does not seem to have an impact at all...
- # once captive-install-acquire has finished, you can prepare the /etc/fstab to include a specific item for your ntfs partition in rw mode:
sudo captive-install-fstab -v --add
- # you can now mount the partition in readwrite mode with:
sudo mount /mnt/captive-noname
|

|
Tips For Compile And Use Opensc
- # a very nice technical guide to openssl user authentication with apache using certificates and smartcards
- # installing opensc:
TARGETDIR=$HOME
mkdir -p $TARGETDIR
cd $TARGETDIR
cvs -z3 -d :pserver:cvs@cvs.opensc.org:/cvsroot co opensc
cd $TARGETDIR/opensc
./bootstrap
./configure
time sudo make install
- # prepare a pkcs#15 card:
debugLevel=-vvvvvv
pkcs15-init $debugLevel -T --erase-card --create-pkcs15 --profile pkcs15 -a 45 -l 45 --pin 1234 --puk 123456 --so-pin 123456 --so-puk 12345678
pkcs15-init $debugLevel -T -P -a 45 -l 45 --pin 1234 --puk 123456 --so-pin 123456 --so-puk 12345678
|

|
Tips To Use Openssl
- # a very nice technical guide to openssl user authentication with apache using certificates and smartcards
- # a very interesting overview with useful examples of commonly used openssl commands: http://resin.csoft.net/cgi-bin/man.cgi?sektion=1&topic=openssl
- # compute the crypt password as used by many unix systems:
openssl passwd
- # generate and print a 1024-bit rsa key pair:
openssl genrsa -out rsa.key.pair 1024
openssl rsa -in rsa.key.pair -text -noout
- # convert a certificate from DER into PEM format:
openssl x509 -in cert.der -inform DER -outform PEM -out cert.pem
- # verify the validity of a certificate using openssl, given a file cacerts.txt which holds a concatenation of trusted ca certificates in PEM format:
openssl verify -CAfile cacerts.txt -purpose any cert1.pem cert2.pem
- # having a look at the content of a certificate revocation list:
openssl crl -in crl.der -inform DER -text -noout|less
- # compiling a sample engine for openssl 0.9.7x:
TARGETDIR=~/openssl
mkdir -p $TARGETDIR
cd $TARGETDIR
wget http://www.openssl.org/source/openssl-0.9.7d.tar.gz
wget http://sunsite.rediris.es/pub/rediris/cert/crypt/misc/rsaref2.tar.gz
tar -xzvf openssl-0.9.7*
cd openssl*/demos/engines
tar -xzvf ../../../rsaref2.tar.gz
mv rsaref2/* rsaref
rmdir rsaref2
cd rsaref
wget http://godot.studentenweb.org/patches/rsaref/patch.rsaref.makefile
patch -p0 < patch.rsaref.makefile
make gnu
# once the engine has been compiled, you can copy into a directory where you keep your shared libraries, e.g.,
mkdir ~/lib
cp librsaref.so ~/lib
# you can now enjoy using your engine as follows:
openssl engine -vvvv dynamic -pre SO_PATH:$HOME/lib/librsaref.so -pre ID:rsaref -pre LIST_ADD:1 -pre LOAD -t -c
fortune > data.txt
openssl md5 -engine rsaref data.txt
# note that it is important to specify the absolute path to the shared library...
|

|
Tips To Set Up An OSGi Framework
- # download the excellent and open-source OSGi gateway framework of http://www.knopflerfish.org/index.html, and store it in /tmp:
cd /tmp
wget http://www.knopflerfish.org/releases/1.0.2/knopflerfish_osgi_1.0.2.jar
export KNOPFLERFISH_BIN=/tmp/knopflerfish_osgi_1.0.2.jar
- # specify where the installation should go:
export KNOPFLERFISH=~/osgi
mkdir -p $KNOPFLERFISH
- # launch the installation program:
cd $KNOPFLERFISH;java -jar $KNOPFLERFISH_BIN -batch
- # running the framework:
cd $KNOPFLERFISH/knopflerfish_osgi_1.0.2/knopflerfish.org/osgi;java -jar framework.jar
|

|
Tips To Manage Your Partitions
- # GRUB mini HowTo, boot loader which is even more powerfull than lilo
- # enumerate all the partitions which are currently known to /proc/partitions:
fdisk -l
- # add ext3 journalling information to some ext2 partition:
tune2fs -j /dev/hda2
- # remove ext3 journalling information from an ext3 partition other than the root partition (have a look at http://www.troubleshooters.com/linux/ext2toext3.htm if you wish to remove ext3 journalling data from the root device):
tune2fs -O ^has_journal /dev/hda2;e2fsck /dev/hda2
- # creating a large vfat partition on your unix box:
mkfs.vfat -F 32 /dev/hda8
- # undelete a file on a vfat partition:
dosfsck -r -u path/file /dev/hdaXX
|

|
perl Tips
- # look for a specific pattern in standard input (binary or text files) and print the pattern's byte-offset:
#!/usr/bin/perl
open(P,"-");
$a=join("",<P>);
while($a =~ m/pattern/gs){
print join(/:/,@-)."\n";
}
close(P);
- # find all common lines in two files (cfr., http://perlmonks.thepen.com/36725.html):
perl -ne 'print if ($seen{$_} .= @ARGV) =~ /10$/' fileA fileB >output
|

|
|
Tips To Use Pgp

|
Installation Guidelines To Enable S/MIME In Pine
|
pine with s/mime, patches for pine4.61 and pine4.60 (produced by myself, based on the ``original'' pine4.58 produced by Jonathan Paisley and Martin Kouril)
- # the following steps prepare the pine configuration files so that you can validate signatures from smiming people using a Belgian eID card :))
mkdir -p ~/.pine-smime/ca ~/.pine-smime/public ~/.pine-smime/private
cd ~/.pine-smime/ca
wget http://certs.eid.belgium.be/belgiumrs.crt
for certificateInDerFormat in *crt
do
openssl x509 -in $certificateInDerFormat -inform der -outform pem -out `basename $certificateInDerFormat`.pem
ln -sf `basename $certificateInDerFormat`.pem `openssl x509 -noout -hash -in $certificateInDerFormat -inform der`.0
rm $certificateInDerFormat
done
Make sure to enable signature verification in pine's configuration file (<M>ain menu, <S>etup, <C>onfig, smime-options: verify-on).
You should also put your trusted root certificates in ~/.pine-smime/ca: place the DER-formatted files in ~/.pine-smime/ca (make sure they are called *.crt), and re-run the for-loop.
If the certificates are already in pem-format (and have the *.pem extension), you can prepare them to use with pine with:
cd ~/.pine-smime/ca
for certificateInPemFormat in *.pem
do
ln -sf $certificateInPemFormat `openssl x509 -noout -hash -in $certificateInPemFormat`.0
done
- # after the configuration files have been set up, you have to prepare pine itself to make it support smime and time stamping. The patch for pine4.61 is the result of Jonathan Paisley, Martin Kouril, Henrik Edlund and Danny De Cock. It is wise to copy and paste the following commands ``step by step''. If your self-compiled pine binary crashes for one reason or another, this problem might be solved rebuilding everything using gcc-2.95:
- # if you have sudo, you might wish to first activate your root privileges (of course after having analyzed and tested the stuff appropriately):
sudo ls
- # initial preparation of the installation directories (the stuff works correctly for me on linux (debian and redhat), osf and cygwin):
UNAME=`uname`
PINEFILES=~/pine.downloads
PINEDIR=~/smime.pine.for.$UNAME
mkdir -p $PINEDIR $PINEFILES
cd $PINEDIR
COMPILER=""
if [ :$UNAME: == :OSF1: ]
then
SYSTEM=osf
fi
if [ :$UNAME: == :Linux: ]
then
SYSTEM=slx
COMPILER="gcc-2.95"
fi
if [ :$UNAME: == :CYGWIN_NT-5.1: ]
then
SYSTEM=cyg
COMPILER="gcc-2.95"
fi
if $COMPILER --version &> /dev/null
then
COMPILER="CC=$COMPILER"
else
COMPILER=""
fi
echo using compiler option :$COMPILER: for this :$UNAME: system
if time ls &> /dev/null
then
TIME=time
else
TIME=""
fi
if sudo ls
then
echo assuming sudo is allowed
SUDO="sudo"
SSLDIR=/usr/local/ssl
OPENSSLPREFIX="--prefix=$SSLDIR"
if [ :$UNAME: == :CYGWIN_NT-5.1: ]
then
BUILDPOSTFIX="cyg SSLDIR=$SSLDIR"
EXTENSION=.exe
else
BUILDPOSTFIX=" SSLDIR=$SSLDIR"
EXTENSION=""
fi
else
echo assuming sudo is not allowed
SUDO=""
if [ :$UNAME: == :CYGWIN_NT-5.1: ]
then
SSLDIR=/usr/local/ssl;
OPENSSLPREFIX="--prefix=$SSLDIR"
BUILDPOSTFIX="cyg SSLINCLUDE=$SSLDIR/include SSLLIB=$SSLDIR/lib"
EXTENSION=.exe
else
SSLDIR=~/openssl
OPENSSLPREFIX="--prefix=$SSLDIR"
BUILDPOSTFIX=" SSLDIR=$SSLDIR SSLCERTS=$SSLDIR/ssl/certs"
EXTENSION=""
fi
fi
- # download the source code of the most recent version of pine, openssl, the time stamping patch for openssl (comes from http://www.opentsa.org/ts/ts-20040320-0_9_7d-patch.gz), etc...
cd $PINEFILES
$TIME wget -N --retr-symlinks ts-20040320-0_9_7d-patch.gz
$TIME wget -N --retr-symlinks ftp://ftp.cac.washington.edu/pine/pine.tar.gz
$TIME wget -N --retr-symlinks http://www.openssl.org/source/openssl-0.9.7d.tar.gz
- # apply the time stamping patches to openssl:
cd $PINEDIR
rm -rf openssl-0.9.7d
$TIME tar -xzf $PINEFILES/openssl-0.9.7d.tar.gz
cd $PINEDIR/openssl-0.9.7d
gzip -dc $PINEFILES/ts-20040320-0_9_7d-patch.gz | $TIME patch -p1
$TIME ./config $OPENSSLPREFIX
$SUDO $TIME make install
- # apply the s/mime patch to pine and compile it:
cd $PINEDIR
rm -rf pine4.61
$TIME tar -xzf $PINEFILES/pine.tar.gz
$TIME wget -N --retr-symlinks smime.patch.for.pine4.61
cd $PINEDIR/pine4.61
cat ../smime.patch.for.pine4.61 | $TIME patch -p2
$TIME ./build$BUILDPOSTFIX $COMPILER $SYSTEM
- # you can now execute the smime-enabled pine:
$PINEDIR/pine4.61/bin/pine$EXTENSION
- # if it works, you can ``install'' it and include it in your default path:
mkdir -p ~/bin.$UNAME
cp $PINEDIR/pine4.61/bin/pine$EXTENSION ~/bin.$UNAME
echo export PATH=~/bin.$UNAME:\$PATH >> ~/.bash_profile
# if it does not work, you might try to compile the stuff again with a different compiler (remember that I got it all working using version 2.95 of gcc), e.g.:
COMPILER="CC=gcc-3.3"
$TIME ./build$BUILDPOSTFIX $COMPILER $SYSTEM
# you can get a list of the compilers with:
find /usr/bin -type f -iname gcc\*
find /usr/local/bin -type f -iname gcc\*
|

|
Project And Time Management
|
TaskJuggler
# the task juggler is a very powerful project management tool that lets the user specify a task juggler project in a simple text format by listing all tasks and their dependencies. This text file is processed by TaskJuggler which produces various reports in html and xml format. The juggler does not only honor the task interdependencies, but also takes resource constraints into account. The user can create task lists, resource usage tables, status reports, project calendars, and project accounting statements by using the program's filtering and reporting algorithms. The program includes tools producing GANTT and Pert charts
Installation
# I got it working on debian following the following steps:
apt-get install
libxml-xslt-perl
apt-get install libpostscript-simple-perl
apt-get install libclass-methodmaker-perl
apt-get install xsltproc
apt-get install docbook-utils
apt-get install jade
./configure --with-kde-support=yes
# apply the patch described on
http://lists.suse.com/archive/taskjuggler-devel/2004-Oct/0011.html to
tjx2gantt/tjx2gantt
make
sudo make install
cd ~/taskjuggler
wget http://www.taskjuggler.org/download/taskjuggler-cvs.tar.bz2
tar -xjf taskjuggler-cvs.tar.bz2
cd taskjuggler-cvs/
./configure
# edit docs/en/Makefile and remove all makefile bodies which call db2html
make
sudo make install
Basic usage
# once the task juggler has been installed, you can start experimenting with your first projects:
mkdir ~/examples
cd ~/examples/
cp -a /usr/local/share/doc/packages/taskjuggler/Examples .
cd Examples/FirstProject
# generating the project overview sheets
taskjuggler AccountingSoftware.tjp
# regenerate the acso.eps and acso_poster.eps
tjx2gantt AccountingSoftware.tjx
|

|
Tips For Ramdisk
- # Ramdisk creation:
- # determine the number of megabytes of the ramdisk, its location and its mount point:
export RAMDISKSIZE=128000
export RAMDISK=/dev/ram
export RAMMOUNTPOINT=/mnt/ram |
- # create the ramdisk (using dd makes sure it does not have holes):
| sudo dd if=/dev/zero of=$RAMDISK bs=1k count=$RAMDISKSIZE |
- # initialize the ramdisk with a filesystem:
| sudo mke2fs -vm0 $RAMDISK $RAMDISKSIZE |
- # activate the new ramdisk:
sudo mkdir -p $RAMMOUNTPOINT
sudo mount $RAMDISK $RAMMOUNTPOINT |
- # change the ramdisk permissions:
| sudo chmod a+rwx /mnt/ram |
- # Swap file creation:
- # determine the number of megabytes of the swapfile and its location (make sure to specify a target location with enough free space to accomodate the swap file!! Creating a swap file on the root filesystem is not recommended...):
export SWAPSIZE=512
export SWAPFILE=/var/run/swapfile.$SWAPSIZE |
- # create the swap file (using dd makes sure the swap file does not have holes):
| sudo dd if=/dev/zero of=$SWAPFILE bs=1M count=$SWAPSIZE && sync && sync |
- # initialize the swap file:
- # check the current swap settings:
- # activate the new swap space:
- # compare the new swap settings with the previous ones:
- # if you wish to use this swap file permanently, you should add it to the /etc/fstab:
| echo $SWAPFILE swap swap default 0 0|sudo bash -c "cat >> /etc/fstab" |
|

|
Tips To Use Screen
|
screen
Features of screen:
- it keeps text-based programs which need interaction with their user running, even when the connection between your client machine and the server you are working on dies for unkown reasons (e.g., if your windows machine suddenly dies)
Elementary usage guidelines:
- # start the screen to make sure you can safely lose your connection while working:
screen
- # open whatever interactive program you like, e.g., an editor or your favourite email program such as pine in the current screen session:
joe /tmp/whatever
- # open another shell window in that same screen session by pressing
ctrl-a c
- # read the man page for screen in this new session:
man screen
- # go back to your editor window:
ctrl-a 0
- # create a third shell window:
ctrl-a c
- # you can go to the next screen with
ctrl-a n
- # you can go to the previous screen with
ctrl-a p
- # you can now detach your screen session in case you wish to do something else:
ctrl-a d
- # once the screen session has been detached, you can also re-attach it:
screen -r
- # if you have a screen session which is active on a remote machine, you can remotely detach it:
screen -d
- # I commonly use the following commands to detach an existing screen session and to re-attach it immediately:
screen -d;screen -r
|

|
|
Scripts

|
Tips For Sed
- # have sed fetch all lines from a text file starting from the sixth line:
sed -n '6,$p' file.txt
- # append line i to line i+1 if line i+1 starts with $PATTERN:
sed ':a;N;$!ba;s/\n$PATTERN/$PATTERN/g' file.txt
- # a list of handy one-liners for the unix stream editor sed can be found at http://www.student.northpark.edu/pemente/sed/sed1line.txt
|

|
Tips For Ssh
- # pushing data to an ssh server:
tar czf - files/directories | ssh user@host "cd /fullpath && tar xzvf -"
- # pushing data to a tar.gz file on a remote ssh server:
tar czf - files/directories | ssh user@host "cat > /fullpath/file.tgz"
- # pulling data from an ssh server:
ssh user@host "tar czf - files/directories" | tar xzvf -
|

|
Tips For Sshd
- # configuring sshd by editing /etc/ssh/sshd_config to minimize break-in potential through the use of weak passwords and cryptographic mechanisms.
# Edit /etc/ssh/sshd_config to make sure that:
- # the use of the ssh protocol verion 1 is disabled and its hostkeys are not specified
- # the password and publickey authentication methods are enabled
- # the list of block ciphers and mac algorithms that can be used is updated
# You can accomplish this if you specify the following lines in your /etc/ssh/sshd_config:
Protocol 2
# HostKey /etc/ssh/ssh_host_key
PasswordAuthentication no
PubkeyAuthentication yes
Ciphers aes256-cbc,aes192-cbc,aes128-cbc,3des-cbc,blowfish-cbc,cast128-cbc,arcfour
MACs hmac-ripemd160,hmac-sha1,hmac-sha1-96
# Paolo Falcioni kindly provided a ready-to use copy of /etc/ssh/sshd_config which already contains this finetuning
|

|
Tips To Get Your Computer's System Clock Properly Synchronized
- # install and run ntpdate:
echo NTPSERVERS="134.58.255.1" >> /etc/default/ntpdate
apt-get install ntpdate
/etc/init.d/ntpdate restart
- # set your machine's time zone correctly:
sudo tzconfig
- # read out the hardware clock of your computer:
sudo hwclock
|

|
Tips For System Recovery
- # bootdisk: provides various boot disks and utilities for both unix and windows system recovery and maintenance
- # Mounting disks with Linux' loopback device, e.g.. mounting the first partition found in a raw disk dump $Dump:
- # assume $Dump points at the hard disk dump (this dump may have been obtained using a command like `dd if=/dev/hda of=$Dump conv=noerror`):
export Dump=/tmp/dump.img
- # have a look at the partition table:
sudo fdisk -u -l $Dump
- # compute the partition offset of the desired partition:
export StartSector=63 # fdisk shows the start sector for each partition it finds
export BytesPerSector=512 # fdisk reports this as the unit size (in bytes)
export Offset=$[$StartSector*$BytesPerSector]
- # mount the partition (e.g., assuming fdisk reported an ntfs or vfat partition, have a look at `cat /proc/filesystems` to know which filesystems your kernel recognizes, and extend the list of partition types to try accordingly):
export MountPoint=/tmp/dump
sudo mkdir -p $MountPoint
for PartitionType in ntfs vfat;do
sudo mount -o loop,ro,offset=$Offset -t $PartitionType $Dump $MountPoint;
done
sudo ls -aRl $MountPoint
- # shell script to create a lilo boot floppy
- # provides a very nice offline nt password and registry editor... Ideal to edit the registry of an NT machine, and to (re)set the password of any user with a valid (local) account on your NT system... Shutdown your computer, boot off the floppydisk or CD (provided by the author of this site), fix the problem, and that's it!!
- # IBM's excellent system recovery page
- # An entry point to *a lot* `how do I...?'-items can be found at http://www.williamaford.com
|

|
Tips For Tape Drives
|
Tape archiving (works for an HP StorageWorks Ultrium 460 using an Adaptec AIC-7892A U160/m (rev 2) SCSI controller)
- # use modconf to load the appropriate module for your scsi adapter (e.g., kernel/drivers/scsi/aic7xxx_old)
- # use modconf to load the module which provides scsi tape support (i.e., kernel/drivers/scsi/st). Once these modules have been loaded successfully, your scsi tape drive and adapter should appear at the end of
dmesg
- # Assume dmesg reports your scsi tape drive as st0:
if [ :$TAPEDRIVE: == :: ];then export TAPEDRIVE=st0;fi
if [ :$REWINDEDTAPE_DEV: == :: ];then export REWINDEDTAPE_DEV=/dev/$TAPEDRIVE;fi
if [ :$UNREWINDEDTAPE_DEV: == :: ];then export UNREWINDEDTAPE_DEV=/dev/n$TAPEDRIVE;fi
- # rewind the current tape:
time mt -f $REWINDEDTAPE_DEV rewind
- # append new data from $DATADIR to the end of the current tape:
time mt -f $REWINDEDTAPE_DEV rewind
time while tar -tzf $UNREWINDEDTAPE_DEV;do date;done #> /tmp/tape.content.txt
time tar -czvf $UNREWINDEDTAPE_DEV --totals --label=":full backup of :$DATADIR: created on `date`:" $DATADIR
- # add $DATADIR to the tape archive without first rewinding the tape:
if [ :$DATADIR: == :: ];then DATADIR=/home;fi
time tar -czvf $UNREWINDEDTAPE_DEV --totals --label=":full backup of :$DATADIR: created on `date`:" $DATADIR
- # rewind the current tape and list its content:
time mt -f $REWINDEDTAPE_DEV rewind
time while tar -tzf $UNREWINDEDTAPE_DEV;do date;done #> /tmp/backup.tape.content.txt
- # restore all data from the current tape, given that it matches $PATTERN:
time mt -f $REWINDEDTAPE_DEV rewind
if [ :$PATTERN: == :: ];then PATTERN=$USER;fi
if [ :$RESTORED: == :: ];then RESTORED="/tmp/restored.from.tape.on.`date`";fi
mkdir -p "$RESTORED"
cd "$RESTORED";time while tar -xzvf $UNREWINDEDTAPE_DEV \*$PATTERN\*;do date;done
- # eject the current tape after rewinding:
time mt -f $REWINDEDTAPE_DEV offline
|

|
Tips For Usb Devices
- # if you want to make sure that usb 2.0 devices are used at their maximum throughput, you should load the ehci-hcd module at boot time:
echo ehci-hcd >> /etc/modules-`uname -r`
|

|
|
Usb Adsl Modems

|
Links To Free Tools Suitable For Forensic Computing
 |
Foundstone provides the best tools I found so far to interpret Microsoft Windows' Internet Explorer index.dat (with Pasco) and cookies files (with Galleta), info2 files which index the recycle bin, and many more... Sources can be downloaded from the ODESSA project (the open digital evidence search and seizure architecture) at http://sourceforge.net/projects/odessa/ |
 |
digital detective provides another collection of very nice free forensic computing tools and utilities (mostly windows) |
 |
e-evidence info provides a nice overview of (mostly windows) programs useful for forensic purposes |
|

|
Vmware
 |
vmware allows you to run multiple operating systems -- simultaneously on a single PC; develop, test, and deploy multi-use applications (client, server, data center) on a single machine; and spend less time configuring and rebooting, more time developing... |
|

|
Tips To Mirror Web Pages
- # recursively fetching all links referred to in a url without including the url's `upper' links and retrieving only files if they are newer than the local version:
wget -r -N --retr-symlinks -np http://url
- # recursively fetching all links referred to in a url without including the url's `upper' links:
wget -r -np http://url
|

|
Scripts I Made To Create And Design This Web Site
This website has been created using my own bash scripts as I could not find any decent and easy-to-use system to design my new website. I consider it the most powerful and versatile website design tool ever created ];-)
The whole website is location independent, i.e., the directory structure can be copied from one webserver to another without having to deal with broken internal links: all internal links are relative to eachother. E.g., I have three copies of this website. You can transparently visit three (almost) identical websites:
There might be minor differences between these copies, as I do not automatically synchronize them.
No other tools or bash commands/constructions than those commonly available on almost all machines have been used on pure text to produce my marvelous (ahum) website.
An exhaustive enumeration: basename, cat, cd, cp, date, dirname, echo, find, for-do-done, grep, if-then-else-fi, mkdir, mv, rm, sed, seq, sort, test, time, touch, uniq, wc, while, zip.
The scripts also launch a few (optional) tools to improve the website's overall quality, look and feel, and to make sure the html pages are consistent with the current (x)html standards:
- checklink, a great but time-consuming tool which nicely discovers dead links, but it produces rather many false positives, e.g., on https urls
- apcalc, an advanced arbitrary precision calculator
- fortune, adds some random fun to the pages
- ispell, to reduce the number of misspelled words
- perl, to determine the dimensions the various logos
- tidy, makes sure that the pages contain syntactically correct html
- wget, to eliminate false dead links reported by checklink
I have based this website's look and feel on the default layout of Diogenes.
|

|
Wifi
|
Configuring your wireless card
# activating your wireless network card (provided your network card is recognized as ath0, and that you are using Knoppix):
- # configure the wireless card (ssid, encryption keys, etc):
wlcardconfig
- # add the following lines to /etc/network/interfaces:
auto ath0
iface ath0 inet dhcp
- # (re)start the network daemon:
sudo /etc/init.d/networking restart
# if you are not using a Knoppix-based system, you could try to enable your wireless networkcard with:
kwifimanager
Configuring your wireless router or access point
- # use a well-chosen SSID (i.e., the string which identifies your wirless network) which does not identify yourself (remember that a wireless network can be discovered from large distances)
- # do not broadcast the SSID
- # use a well-chosen WEP encryption key (at least 128-bit WEP)
- # protect the access to the configuration interface of your wireless router or access point with a (non-default) password
|

|
Tips and Tricks For Non-windows Experts
- # have a look at the excellent table of equivalents/replacements/analogs of windows software in linux
- # use the Files and Settings Transfer Wizard to back up your windows xp profile for recovery or reinstallation: Start the Files and Settings Transfer Wizard (go to Start, Programs, Accessories, System Tools, and click File and Settings Transfer Wizard; alternatively, you can type from the command prompt:
| C:\WINDOWS\system32\usmt\migwiz.exe |
- # figure out your network settings on xp:
| C:\WINDOWS\system32\ipconfig.exe /all |
- # include the euro symbol in your microsoft excel spreadsheet (given keyboard layout us-101):
- # include the euro symbol in your microsoft word documents:
Follow the following path to launch an easy to use application which gives you many more symbols that you can easily paste: Start -> Programs -> Accessories -> System tools -> Character map
- # unix utilities for windows: GNU utilities for Win32
- # ltools: accessing your ext2 partition from windows given a java gui (caveat: it kills my xp box as soon as the application terminates, i.e., it is better to reboot the machine rather than to close the application).
You can better use explore2fs.exe!!
- # explore2fs.exe allows yo to browse a linux ext2 file system with a windows explorer-like interface
|

|
|
Handy Tools For Windows Users

|
Wiping Data
 |
wipe, a unix tool for secure data deletion |
|

|
Tips For X11
- # the following shortcut restarts the X-server which is currently active on your console:
Note that this shortcut logs out the user of the X-server. This method is particularly useful to punish people who use a screen locker on machines which should be shared among different people

- # usb mouse troubleshooting: It may happen that the automatically generated file /etc/X11/XF86Config-4 does not include correct settings for your usb mouse. If the command
| cat /dev/input/mice|hexdump|timeout 30 head -5 |
outputs some data in hexadecimal format when moving your usb mouse, you may try to configure the mouse-specific sections of /etc/X11/XF86Config-4 by hand, e.g., given the following:
Section "ServerLayout"
Identifier "XFree86 Configured"
Screen 0 "Screen0" 0 0
InputDevice "Keyboard0" "CoreKeyboard"
# PS/2 Mouse not detected
# Serial Mouse not detected
InputDevice "USB Mouse" "CorePointer"
EndSection
Section "InputDevice"
Identifier "USB Mouse"
Driver "mouse"
Option "Device" "/dev/input/mice"
Option "SendCoreEvents" "true"
Option "Protocol" "IMPS/2"
Option "ZAxisMapping" "4 5"
Option "Buttons" "5"
EndSection
- # nice X11 configuration tool for Knoppix:
- # nice /etc/X11/XF86Config generation tool used by Knoppix:
- # if you wish to specify an additional X display which can be accessed through ctrl+alt+8, you could add the following line to /etc/X11/xdm/Xservers:
| :1 local /usr/X11R6/bin/X vt8 -dpi 100 -nolisten tcp |
- # installing the xv.rpm:
- # fetch and unpack the rpm:
- # install the stuff:
| sudo alien /tmp/xv-3.10a-13.i386.rpm |
- # you could also give it a try compiling and installing xv yourself:
- # fetch and unpack the sources:
- # read the README and INSTALL files, and pay the registration fee of 25 dollar
- # replace 'extern char *sys_errlist[]; /* this too... */' by 'extern __const char *__const sys_errlist[];':
cat xv.h|sed s/"extern char \*sys_errlist\[\]; \/\* this too... \*\/"/"extern __const char \*__const sys_errlist\[\];"/ > xv.h.tmp;
mv xv.h.tmp xv.h |
- # make sure that the X11 libraries are found:
cat Makefile|sed s/"LIBS = -lX11 \$(JPEGLIB) \$(TIFFLIB) -lm"/"LIBS = -L\/usr\/X11R6\/lib -lX11 \$(JPEGLIB) \$(TIFFLIB) -lm"/ > Makefile.tmp
mv Makefile.tmp Makefile |
- # execute the make file and install the stuff if successful:
if make;then
sudo mkdir -p /usr/local/man/man1;
sudo make install;
fi |
|

|
 click Here To See All My Bookmarks
click Here To See All My Bookmarks










![tab browser extensions</a>, provides an advanced configuration tool for the tabs bar. This extension can place the tabs bar at the bottom of the browser, which makes FireFox look and behave much like opera ];-) tab browser extensions</a>, provides an advanced configuration tool for the tabs bar. This extension can place the tabs bar at the bottom of the browser, which makes FireFox look and behave much like opera ];-)](../../images/tabBrowserExtensions.png)








 http://eciadsl.flashtux.org/download.php?lang=en
http://eciadsl.flashtux.org/download.php?lang=en





